TL;DR
|
Did you know that 43% of data breaches start inside the organization, often during testing or analytics?
As businesses scale, so does the volume of sensitive information they collect, including names, emails, credit card numbers, and health records. While production systems may be secure, internal teams often work with cloned or raw datasets in environments that don’t have the same protection. This gap becomes a significant weakness.
According to the IBM 2024 Cost of a Data Breach Report, the global average cost of a data breach has risen to $4.45 million, with mishandled personal data being a primary cause.
So, how do you protect data without slowing down your team?
Data masking helps you use realistic, structured, and secure data for development, testing, and analysis without exposing any real user information.
This blog will discuss real-world data masking examples from industries such as banking, healthcare, and analytics. Whether building dashboards or testing software, you’ll learn to apply masking correctly and avoid costly mistakes.
How Data Masking Keeps Your Business Secure and Compliant
Data masking is the process of changing sensitive information to protect it while allowing it to be used for tasks like testing or analysis.
It involves replacing or altering sensitive data so that unauthorized people cannot access the real information, but the data still serves its intended purpose for authorized users.
For example, a database may contain customer names, credit card numbers, or medical records that must be hidden for privacy but must still be accessible for business functions.
Types of Data Masking
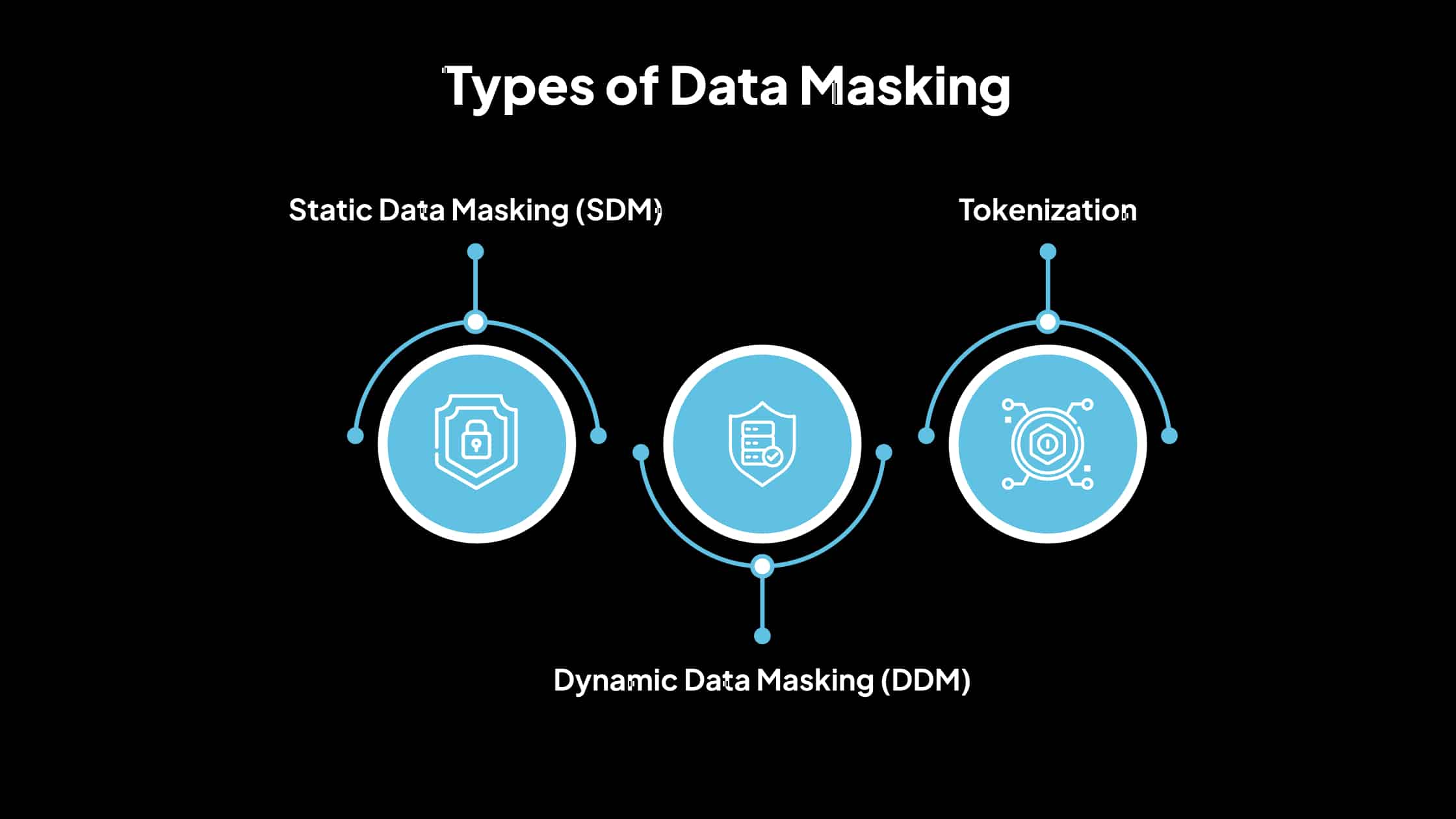
1. Static Data Masking (SDM)
In static data masking, a copy of the original data is created, and sensitive information is replaced with fake, realistic-looking data. This data is used in environments like testing or development, where real data is unnecessary.
For example, a testing team may use a database with fake customer names and addresses instead of real ones, ensuring no personal details are exposed.
2. Dynamic Data Masking (DDM)
The original data remains intact with dynamic data masking, but access to sensitive data is controlled. When someone tries to view sensitive information, it is masked in real time based on the user’s permissions.
For example, when handling a support request, a customer service agent may see only part of a customer’s credit card number, while the rest of the data remains hidden.
3. Tokenization
Tokenization replaces sensitive information with non-sensitive placeholders or “tokens” that cannot be reverse-engineered without special access. These tokens are used in applications in place of the original data.
For example, in payment systems, a real credit card number might be replaced by a random token without meaning outside the system, keeping the original card number secure.
Importance of Data Masking in Ensuring Compliance
Data masking is essential for businesses to follow privacy laws and data protection regulations, such as GDPR (General Data Protection Regulation) and HIPAA (Health Insurance Portability and Accountability Act). These regulations require businesses to safeguard sensitive information like personal data and medical records to prevent unauthorized access and potential misuse.
Here’s how data masking helps in compliance:
- Protects Personal Information
Data masking hides sensitive details so only authorized users can see the original data. This is crucial for maintaining privacy and security.
- Reduces the Risk of Data Breaches
If a data breach occurs, the masked data ensures that no real personal information is exposed, lowering the risk of harm.
- Allows Safe Data Sharing
Businesses can share data for tasks like testing or analysis without violating privacy laws, as the data is anonymized or masked, ensuring it remains protected.
- Supports Legal Requirements
Many regulations require organizations to take measures to prevent the exposure of sensitive data. Data masking helps meet these requirements by ensuring that even if data is accessed, it is not in its original, identifiable form.
5 Real-World Data Masking Examples for Developers and Analysts
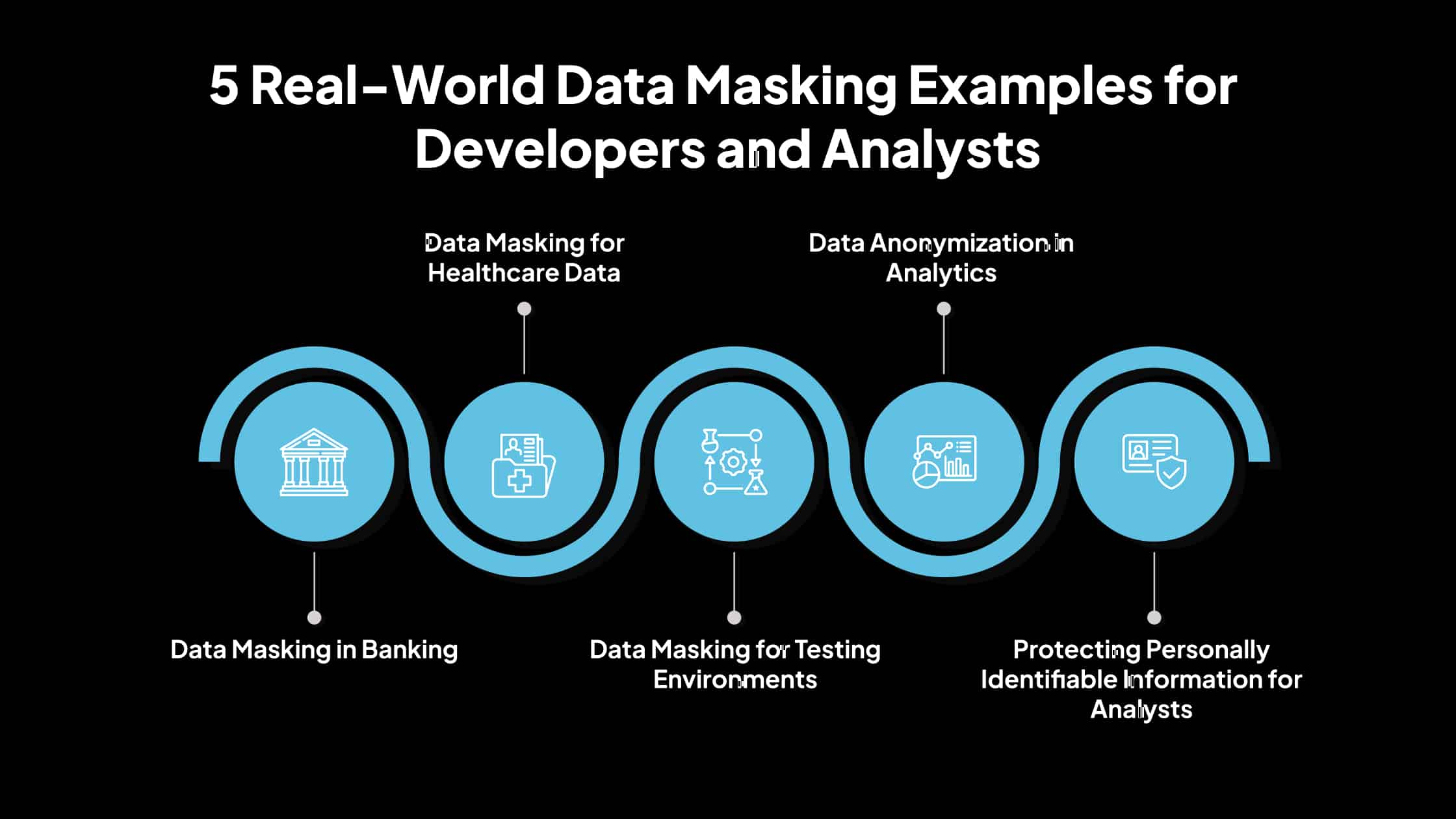
Here are some data masking examples showing how developers and analysts use this technique in real-world situations.
1. Data Masking in Banking
Banks manage sensitive financial data, including customer account details, transaction records, and credit card information. This data is critical for various operations, such as reporting, analysis, and testing, but exposing it to unauthorized individuals could lead to security breaches and privacy violations.
Banks use data masking to safeguard sensitive information while allowing internal teams and third parties to perform necessary tasks like analysis and testing. This technique hides sensitive data by replacing it with masked versions that preserve its structure but remove its real-world identity.
For example, while customer account numbers are needed for analysis, the real account numbers should not be exposed.
Techniques Used in Data Masking in Banking
-
Substitution
This method replaces real account numbers with random values that follow the same format as the original data.
For example, if an account number is 1234-5678-9876, the masked version could be 4321-8765-1234. While these values look like real account numbers, they do not correspond to actual accounts. This ensures that testing or analysis does not expose customer accounts or financial information.
-
Shuffling
Shuffling involves rearranging data, such as transaction amounts and dates, within a dataset. The values remain realistic and follow the original structure, but they are no longer linked to the original transactions.
For example, a 500 transaction made on January 1st, 2025, could be shuffled with a $300 transaction from another date. This way, the transaction data can still be used for analysis or testing without revealing the real transaction history of any customer.
2. Data Masking for Healthcare Data
Healthcare providers are required to comply with privacy regulations like HIPAA to protect patient confidentiality. These regulations apply to all forms of healthcare data, including medical records, treatment plans, and personal details.
Data masking allows healthcare organizations to anonymize data while retaining its usefulness for research, training, and analysis to prevent unauthorized access to sensitive patient information.
Techniques Used in Data Masking For Healthcare
-
Nulling Out
This technique replaces sensitive fields like social security numbers (SSN), diagnosis codes, and patient names with null values or placeholders.
For example, a patient’s SSN (123-45-6789) could be replaced with “XXX-XX-XXXX,” effectively hiding the real value. This approach ensures that sensitive identifiers are not exposed during analysis or sharing, allowing other parts of the data, such as treatment records, to be used.
-
Randomization
Randomization involves changing identifiable data, such as patient names or dates of birth, but keeping the general structure intact.
For example, a patient’s name (Sana Willey ) could be replaced with a randomized name (Alex Charles). Similarly, a date of birth (January 15, 1980) could be randomly changed to another date (March 23, 1985).
This method allows healthcare organizations to protect personal information while retaining the authenticity of other relevant medical data, such as treatment history and outcomes, for research and analysis.
3. Data Masking for Testing Environments
Developers often need access to production-like data when testing applications to ensure they work correctly under real-world conditions. However, sharing real customer or employee data in a test environment can lead to significant privacy and security risks, especially if sensitive information such as personal identification numbers, credit card details, or private addresses is exposed.
To address this issue, developers use data masking to obfuscate sensitive information while preserving the data structure necessary for realistic testing. This allows developers to test features and performance without compromising sensitive customer or employee details.
Techniques Used in Data Masking For Testing Environments
-
Tokenization
Tokenization involves replacing sensitive data, such as payment card details, with randomly generated tokens that still follow the original data format.
For example, a real credit card number (e.g., 4111-1111-1111-1111) could be replaced by a randomly generated token like “T12345-67890,” which maintains the structure of a credit card number but is not tied to any real account. This allows the application to be tested for transactions, payment gateway integration, and error handling without exposing sensitive information.
-
Shuffling
Shuffling involves rearranging data within the dataset, such as customer names, product orders, and transaction amounts.
For instance, customer names might be mixed up, so the system will only deal with randomized associations instead of matching real names with real transaction data. This allows developers to test how the system handles customer data and orders without using actual customer identities, maintaining realism while keeping the data anonymous.
4. Data Anonymization in Analytics
Analysts often require access to large datasets to conduct meaningful analysis and generate insights. However, these datasets may contain sensitive information that must remain protected, such as personal identification details or financial records.
Data anonymization techniques, including data masking, allow analysts to work with realistic datasets that preserve the integrity of the data necessary for analysis but protect any sensitive information. Analysts can perform their work anonymously without risking privacy violations or non-compliance with data protection regulations by anonymizing sensitive identifiers.
Techniques Used in Data Anonymization in Analytics
-
Data Masking for Data Analysts
This technique replaces personally identifiable information (PII) such as customer names, addresses, and email IDs with generic placeholders or pseudonyms. F
For instance, customer names (e.g., Smith ) are replaced with randomized names (e.g., William), and email addresses are replaced with random strings like “user1234@company.com.” Analysts can still perform behavioral or transactional analysis without exposing real customer data.
-
Generalization
Generalization is the process of replacing exact values with broader categories or ranges. For example, rather than using an exact customer age (e.g., 35), the data might be generalized to an age range (e.g., 30-40).
Similarly, instead of using an exact purchase amount (e.g., $257.34), the data might be generalized into price ranges (e.g., $200-$300). This helps analysts conduct demographic or market trend analysis without needing precise, identifiable data, thus ensuring privacy.
5. Protecting Personally Identifiable Information for Analysts
Data analysts often require access to datasets containing personally identifiable information (PII) for tasks such as segmentation, behavior analysis, and market research. However, sharing and accessing PII carries significant risks related to privacy violations and non-compliance with data protection regulations (e.g., GDPR, CCPA). Analysts must be able to work with real data while ensuring that sensitive personal details are protected to avoid privacy breaches.
Data masking techniques anonymize sensitive information within the dataset to enable analysts to perform their tasks without compromising privacy. By masking PII, businesses can ensure compliance with privacy laws while allowing analysts to perform necessary data-driven tasks, such as customer segmentation and market analysis.
Techniques Used In Protecting PII
-
Substitution
Substitution involves replacing sensitive PII with generic placeholders or pseudonyms like email addresses and phone numbers.
For example, a real email address (e.g., john.doe@example.com) might replace a randomized placeholder such as “user1234@company.com.” Similarly, phone numbers can be replaced with dummy numbers (e.g., 555-000-0000) to prevent unauthorized access to actual contact details. This ensures the dataset can be analyzed while keeping the PII hidden.
-
Nulling Out
Nulling out involves masking sensitive fields, such as customer names, phone numbers, or addresses, by replacing them with null values or empty placeholders. For instance, a mailing address could be replaced with a null value (e.g., “N/A” or an empty string).
This technique ensures that analysts do not expose sensitive information during their analysis or reporting. While some fields are completely hidden, the data remains usable for non-sensitive tasks such as analyzing customer purchase behavior or engagement patterns.
How to Implement Data Masking: Best Practices
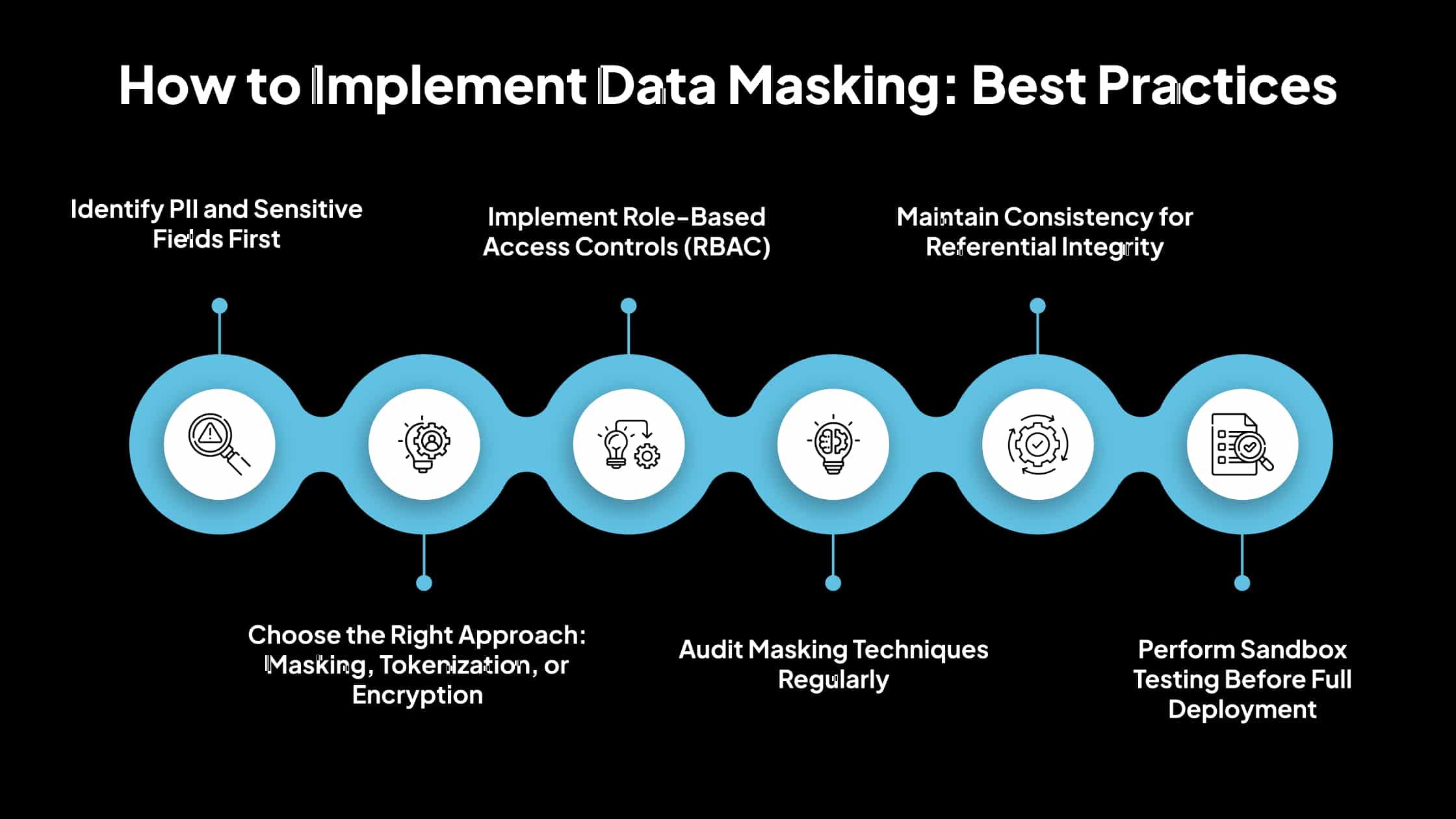
Here is the list of data masking implementation best practices to help you protect sensitive data effectively while maintaining data usability.
1. Identify PII and Sensitive Fields First
Before anything else, you need to know what data you’re protecting. Personally Identifiable Information (PII) includes names, email addresses, national ID numbers, health records, and financial details.
According to a Verizon Data Breach Investigations Report, 80% of data breaches involve stolen or misused credentials and personal data, underscoring the importance of identifying sensitive fields before masking.
A data discovery tool or classification engine can help flag high-risk columns across databases. For example, in a healthcare environment, PHI like patient IDs and diagnoses must be masked differently from general operational data.
2. Choose the Right Approach: Masking, Tokenization, or Encryption
Not all sensitive data requires the same level of obfuscation. Select your protection strategy based on the use case:
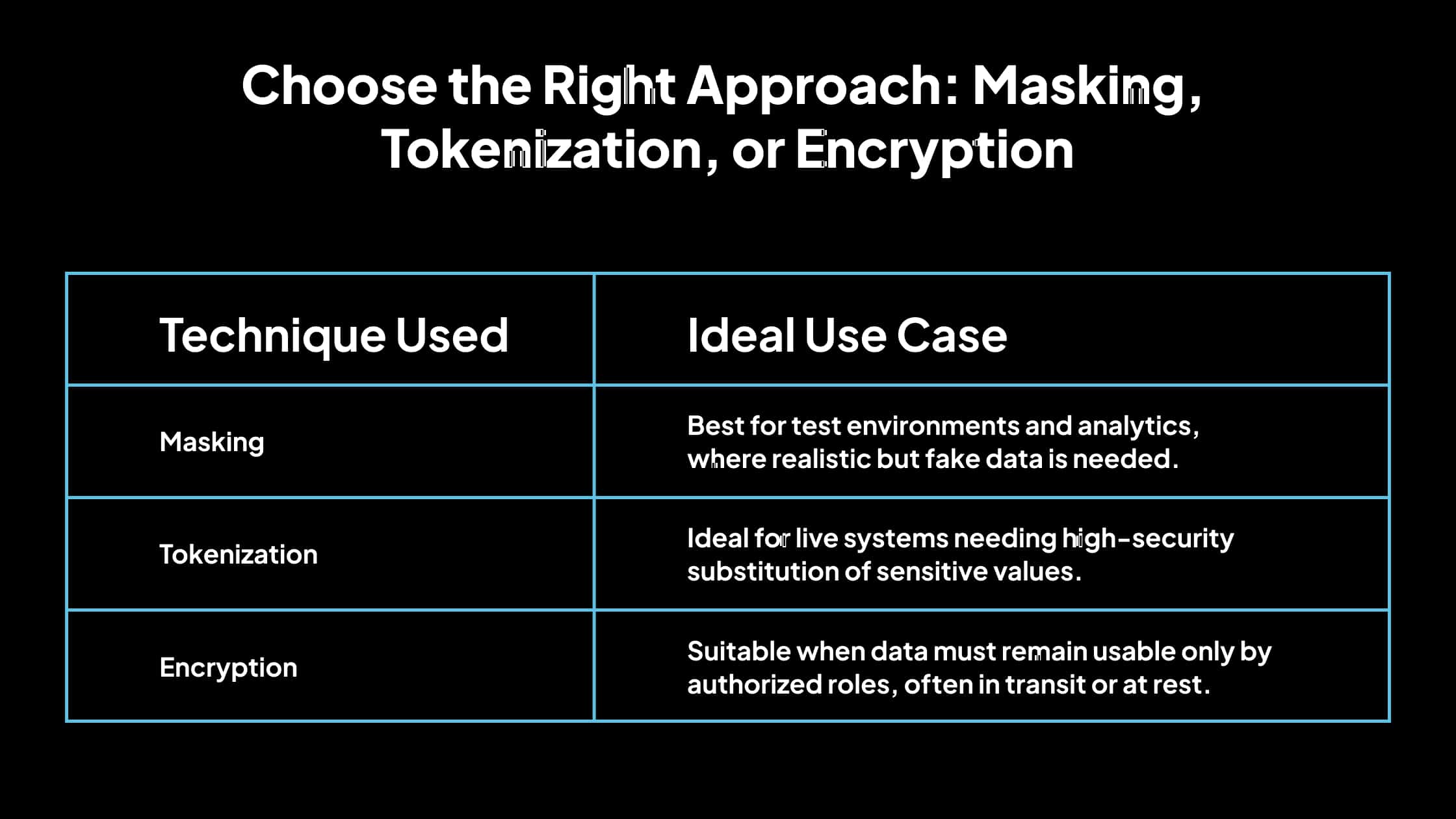
A 2023 Ponemon Institute study found that organizations using layered methods like masking and encryption experienced 30% fewer data leakage incidents than single methods.
3. Implement Role-Based Access Controls (RBAC)
Even masked data can be misused if access is too broad. With RBAC, users only see the data they are permitted to, based on their roles. This ensures developers or analysts can use masked data effectively without seeing the original PII.
For instance, a QA engineer testing payment flows may need masked credit card numbers, while
A compliance officer may require access to real data under strict logging.
4. Audit Masking Techniques Regularly
Data environments evolve, new fields are added, and applications change. If you don’t regularly audit your masking, sensitive data may leak through gaps. Set up automated audits to validate that masking is applied wherever PII exists.
According to Gartner, regular audits can reduce the risk of non-compliance fines by up to 40%, especially in industries governed by regulations like GDPR, HIPAA, or PCI-DSS.
5. Maintain Consistency for Referential Integrity
Maintaining relationships is crucial when masking multiple tables. For instance, a masked customer ID in one table should map consistently across all relevant tables to preserve analytical accuracy.
Inconsistent masking can break foreign key relationships and degrade reporting.
Use deterministic masking or look-up tables to ensure consistent pseudonyms are applied, mainly for analytics and machine learning tasks.
6. Perform Sandbox Testing Before Full Deployment
Before pushing masked data into test or analytics environments, simulate real-world scenarios in a sandbox. This helps validate whether the data retains its functional shape, relationships and logic hold up under business rules, and masking didn’t unintentionally corrupt functional data structures.
According to a 2022 IBM security report, testing in a controlled sandbox environment can reduce post-deployment issues by up to 50%.
Challenges in Data Masking and How to Overcome Them
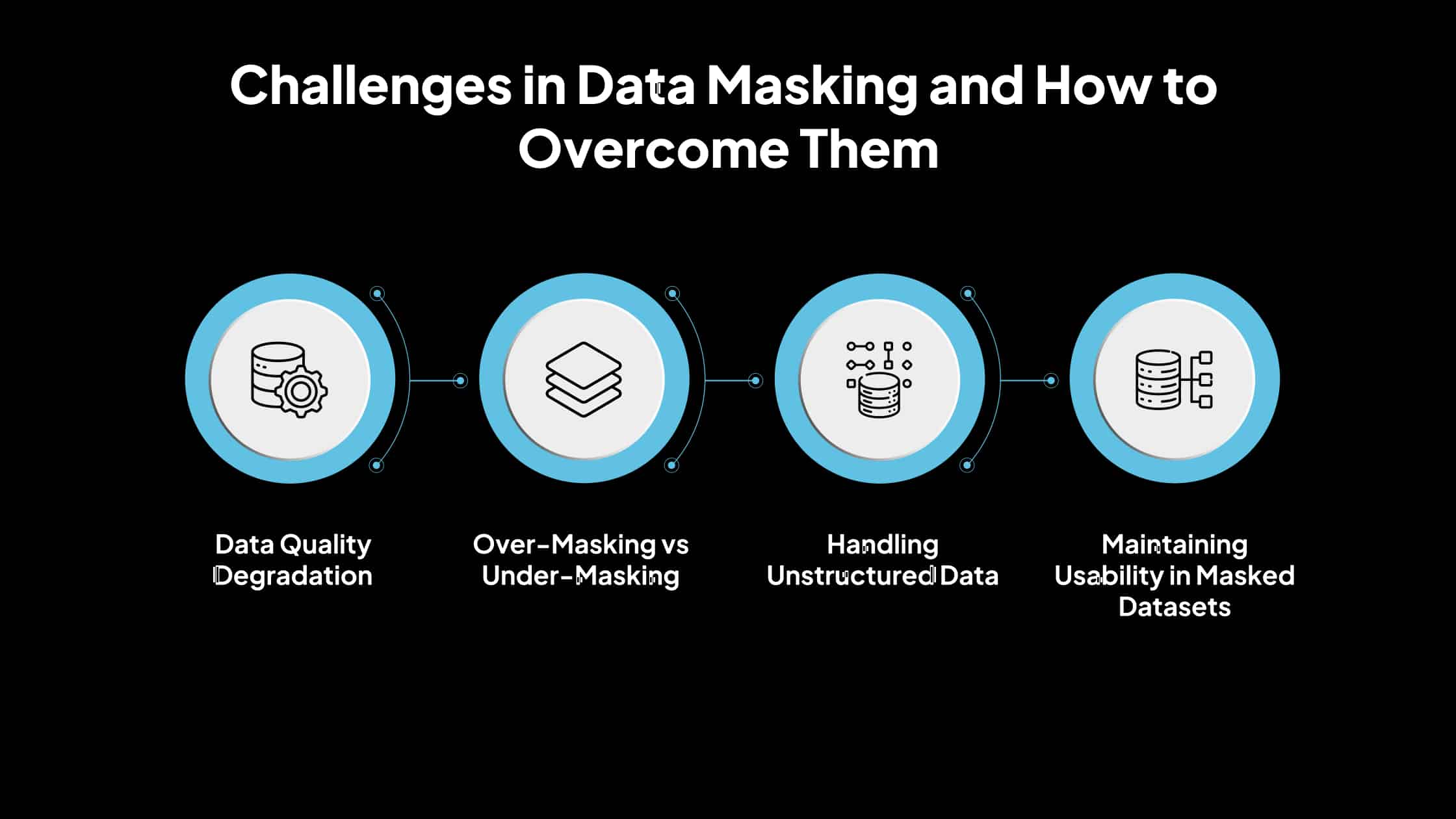
While data masking is vital in protecting sensitive information, implementing it comes with challenges. Below are some of the most common issues organizations face:
1. Data Quality Degradation
Masking can reduce data quality, when formats or dependencies are not preserved. This can affect testing, analytics, and reporting accuracy.
Use format-preserving masking techniques to retain data structure (e.g., date formats, numeric ranges). Also, post-masking validation rules should be implemented to ensure the masked data behaves similarly to the original.
2. Over-Masking vs Under-Masking
Over-masking can make data unusable, while under-masking exposes sensitive fields to risk. Striking the right balance is difficult, especially in complex datasets.
Conduct a data risk assessment to classify fields by sensitivity. Apply masking only where required and use role-based masking levels, so different users see different versions of data based on access rights.
3. Handling Unstructured Data
Unstructured data (e.g., emails, scanned documents, notes fields) is harder to mask because PII can appear in unpredictable formats.Use natural language processing (NLP) or pattern-matching tools to locate and redact sensitive data in unstructured text. Apply custom masking rules specific to your data sources.
4. Maintaining Usability in Masked Datasets
Masked data often loses usefulness, especially for analytics, machine learning, or software testing. Loss of data integrity can skew results.Apply consistent and deterministic masking where relationships must be preserved (e.g., the same masked customer ID across multiple tables). Generate synthetic data when the original data is too sensitive, but structural similarity is required.
Why Choose Avahi Data Masker: Streamlined, Scalable, and Secure Data Masking
As part of its commitment to secure and compliant data operations, Avahi’s AI platform offers tools that help organizations manage sensitive information precisely and accurately. One of its standout features is the Data Masker, designed to protect financial and personally identifiable data while supporting operational efficiency.
Avahi Data Masker is built for organizations that must handle sensitive information securely without compromising operational efficiency. It offers a structured, AI-powered approach to data masking, ensuring that confidential fields, such as personal identifiers, financial records, and health data, are protected while remaining usable for internal processes like analytics, development, and testing. Here are the reasons to choose Avahi Data Masker:
- Cross-Industry Compliance Support: Enables secure data handling across healthcare (HIPAA), finance (PCI DSS), retail, and other regulated sectors.
- Role-Based Access Control: Restricts data visibility to authorized users, ensuring sensitive data is protected during multi-team or vendor access.
- AI-Powered Masking Logic: Uses intelligent algorithms to identify and mask sensitive fields without altering data structure or usability.
- Simple, Guided Workflow: A user-friendly interface streamlines the process from file upload to secure output.
- Data Usability Post-Masking: Masked data retains its format, supporting downstream tasks such as reporting, fraud detection, or test environments.
This functionality ensures data security, regulatory alignment, and operational continuity in one solution.
Simplify Data Protection with Avahi’s AI-Powered Data Masking Solution
At Avahi, we understand the critical importance of safeguarding sensitive information while ensuring seamless operational workflows.
With Avahi’s Data Masker, your organization can easily protect confidential data, from healthcare to finance, while maintaining regulatory compliance with standards like HIPAA, PCI DSS, and GDPR.
Our data masking solution combines advanced AI-driven techniques with role-based access control to keep your data safe and usable for development, analytics, and fraud detection.
Whether you need to anonymize patient records, financial transactions, or personal identifiers, Avahi’s Data Masker offers an intuitive and secure approach to data protection.
Ready to secure your data while ensuring compliance? Get Started with Avahi’s Data Masker!
Frequently Asked Questions
1. What are some real-world data masking examples used in different industries?
Real-world data masking examples include techniques like substitution and shuffling in banking, nulling out patient information in healthcare, tokenizing testing environments, and generalization methods in analytics. These techniques help protect sensitive data while keeping it usable for development and analysis.
2. How is data masking used in banking to protect customer information?
In data masking for banking, techniques such as substitution and shuffling are used to protect sensitive financial data like account numbers and transaction histories. These methods help banks maintain compliance while ensuring analysts and developers can work with realistic, structured data.
3. Why is data masking important in healthcare data management?
Data masking for healthcare data helps anonymize personal details like patient names, SSNs, and diagnosis codes. By applying techniques like randomization and nulling out fields, healthcare providers can comply with regulations like HIPAA while still using data for research, training, or system testing.
4. How does data masking help in software testing environments?
Data masking for testing environments allows developers to use realistic data formats without exposing real customer or employee information. Techniques like tokenization and shuffling enable safe and accurate application testing by preserving data structure while protecting privacy.
5. What are the best practices for protecting PII for analysts using data masking?
When protecting PII for analysts, it’s essential to use data masking techniques like substitution, nulling out, and generalization. These help analysts perform segmentation and behavioral analysis without violating privacy regulations or exposing real user identities.