TL;DR
|
Over 8.2 billion data records were breached in 2023, with nearly 70% containing personal identifiers, including names, email addresses, and ID numbers. These numbers represent real legal, financial, and reputational risks for businesses.
With the General Data Protection Regulation (GDPR) in force, exposing personal data is a compliance violation.
GDPR mandates that organizations must secure personal data through technical measures, such as pseudonymization, minimization, and privacy by design. This is where data masking becomes essential.
GDPR masking data helps in systematically replacing sensitive fields with non-identifiable equivalents while maintaining data usability for testing, analytics, or vendor sharing.
When done correctly, it prevents unauthorized access, reduces the impact of breaches, and supports the core security and accountability principles of the GDPR.
In this blog, you’ll explore what data masking is, how it functions in practical business environments, the essential GDPR articles it aligns with, and the best practices for implementing GDPR-compliant masking strategies effectively. If your business processes any form of personal data, whether in testing, outsourcing, or analytics, understanding GDPR-compliant data masking is a compliance necessity.
Understanding Data Masking: A Strategic Priority for Data-Driven Companies
Data masking is the process of transforming sensitive data elements, such as personally identifiable information (PII), financial records, or health information into a modified version that retains the original data format while concealing the original values. The purpose is to ensure that sensitive data is not exposed to unauthorized individuals during development, testing, training, or analytics processes. Examples of data commonly masked are:
| PII | Names, Social Security Numbers, email addresses, phone numbers. |
| Financial Information | Credit card numbers, bank account details, and transaction histories. |
| Healthcare Data | Patient IDs, medical histories, and lab results. |
For instance, consider the way credit card numbers are partially hidden on e-commerce websites: **** **** **** 1234. The masked portion is replaced, yet the format is preserved to allow processing or display continuity. Similarly, in surveillance footage, identifiable facial features are often blurred to protect individual identities while retaining context.
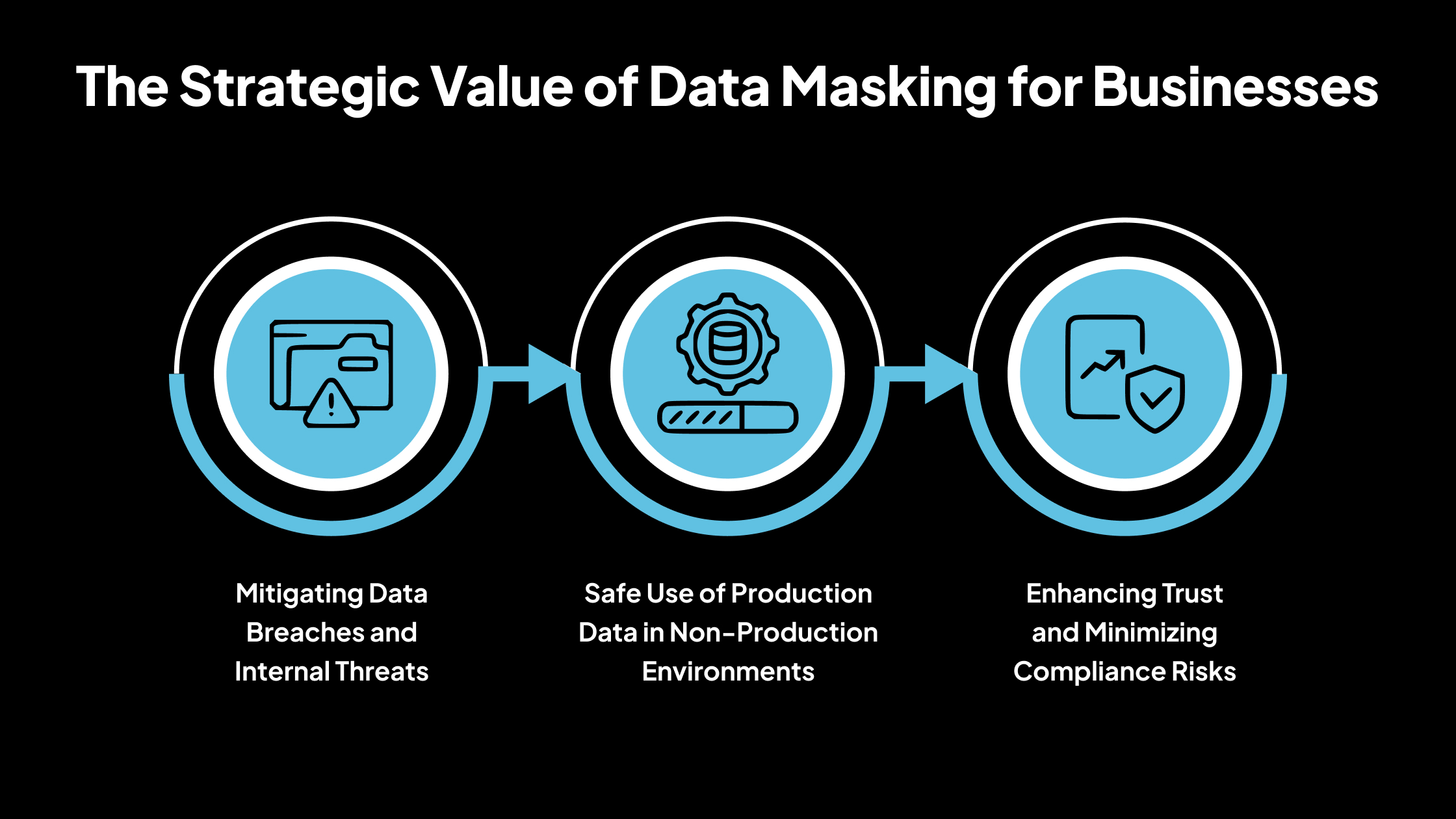
The Strategic Value of Data Masking for Businesses
As organizations increasingly rely on large-scale data operations for development, analytics, and third-party collaboration, ensuring that personal and confidential information is not exposed becomes essential.
Below is a breakdown of why data masking is essential for ensuring both data security and GDPR compliance in modern enterprise operations.
Mitigating Data Breaches and Internal Threats
Even with perimeter security measures such as firewalls and intrusion detection systems, unauthorized access can still occur, especially from internal actors with elevated permissions. According to data breach investigations, a significant percentage of incidents originate from within the organization.
By transforming personally identifiable information (PII), financial records, or health data into non-identifiable values, data masking ensures that even if unauthorized access occurs, the exposed data holds no real value.
Masking limits the surface area of data loss prevention (DLP) concerns by decoupling data usability from its sensitivity, thereby reducing the potential for data loss.
For example, suppose a developer or analyst gains access to a customer support database that includes masked contact details such as userxyz@demo.com instead of alex.doe@actualdomain.com. In that case, the risk of identity exposure is neutralized, reducing the chances of GDPR data privacy violations.
Safe Use of Production Data in Non-Production Environments
Organizations often replicate production databases into development, testing, or training environments to maintain data integrity for performance or functionality testing. However, these environments typically lack the same level of access control and monitoring as live systems.
Developers, QA engineers, or external vendors might unintentionally access real customer or employee data. Logs or debug files might store exposed data in plaintext, increasing risk during audits.
Static data masking is applied before production data is copied, ensuring that test environments do not contain sensitive data. This allows development teams to test with real-world data structures while complying with regulatory requirements such as Article 25 of the GDPR (data protection by design and by default).
Enhancing Trust and Minimizing Compliance Risks
Maintaining the confidentiality of sensitive data is a cornerstone of trust with customers and stakeholders. Non-compliance with privacy laws, such as the General Data Protection Regulation (GDPR), can result in legal penalties, reputational damage, and operational disruptions.
Under GDPR, unauthorized access to unmasked personal data triggers mandatory breach notifications and potential fines (up to €20 million or 4% of annual turnover). Data masking supports GDPR compliance by enabling pseudonymization, a practice recognized under Article 4(5) and Article 32 as a safeguard for data processing.
This reduces the need to report a data breach if the compromised data was adequately protected or anonymized and facilitates data minimization techniques, helping businesses retain only necessary and de-identified information.
Essential GDPR Articles That Shape Enterprise Data Protection Practices
The General Data Protection Regulation (GDPR) is a data privacy law implemented by the European Union (EU) that came into effect on May 25, 2018.
It helps to protect the personal data of individuals within the EU. It applies to all organizations, both inside and outside the EU, that handle the data of EU residents. The GDPR establishes a standardized framework for data protection, requiring organizations to collect, process, and store personal data responsibly and securely.
The core goals of GDPR are to protect individuals’ personal data and privacy rights and provide transparency in how personal data is collected, used, and stored, grant individuals control over their data, including rights to access, correct, or delete it and hold organizations accountable for data protection through precise legal requirements and enforcement mechanisms.
GDPR Articles Relevant to Data Security
Article 5 – Principles Relating to Processing of Personal Data
Article 5 outlines fundamental principles that must guide data processing:
- Data must be collected and used lawfully and in a clear, fair manner.
- Data should only be collected for specific, explicit, and legitimate purposes.
- Only the data needed for the intended purpose should be collected.
- Personal data must be accurate and kept up to date.
- Data must not be kept longer than necessary.
- Data must be protected against unauthorized access or loss.
- The organization must be able to demonstrate compliance with these principles.
This supports data minimization techniques by reducing the exposure of real data and helps maintain integrity and confidentiality in test and analytics environments.
Article 25 – Data Protection by Design and by Default
According to Article 25, organizations are required to integrate data protection into their systems and processes from the outset, rather than as an afterthought.
Data protection features should be integrated during system design (e.g., masking, pseudonymization). Default settings should ensure that only the minimum necessary data is collected and shared.
Data masking supports privacy by design, especially in software development and database access control.
Article 32 – Security of Processing
Article 32 requires organizations to implement appropriate technical and organizational measures to ensure a level of security commensurate with the risk.
Measures may include encryption, pseudonymization, access control, regular testing and evaluation of security systems. This article is recognized under technical safeguards, particularly when paired with pseudonymization and helps reduce the impact of unauthorized access.
Article 33 – Notification of a Personal Data Breach to the Supervisory Authority
According to Article 33, Organizations must notify their relevant Data Protection Authority (DPA) within 72 hours of becoming aware of a personal data breach.
If data is adequately masked or pseudonymized, the breach may not require reporting, depending on risk assessment.
Article 34 – Communication of a Personal Data Breach to the Data Subject
According to Article 34, if a breach is likely to result in a high risk to individual rights or freedoms, the affected individuals must also be informed without undue delay.
Effective masking may eliminate or reduce the risk to individuals, potentially removing the obligation to notify them.
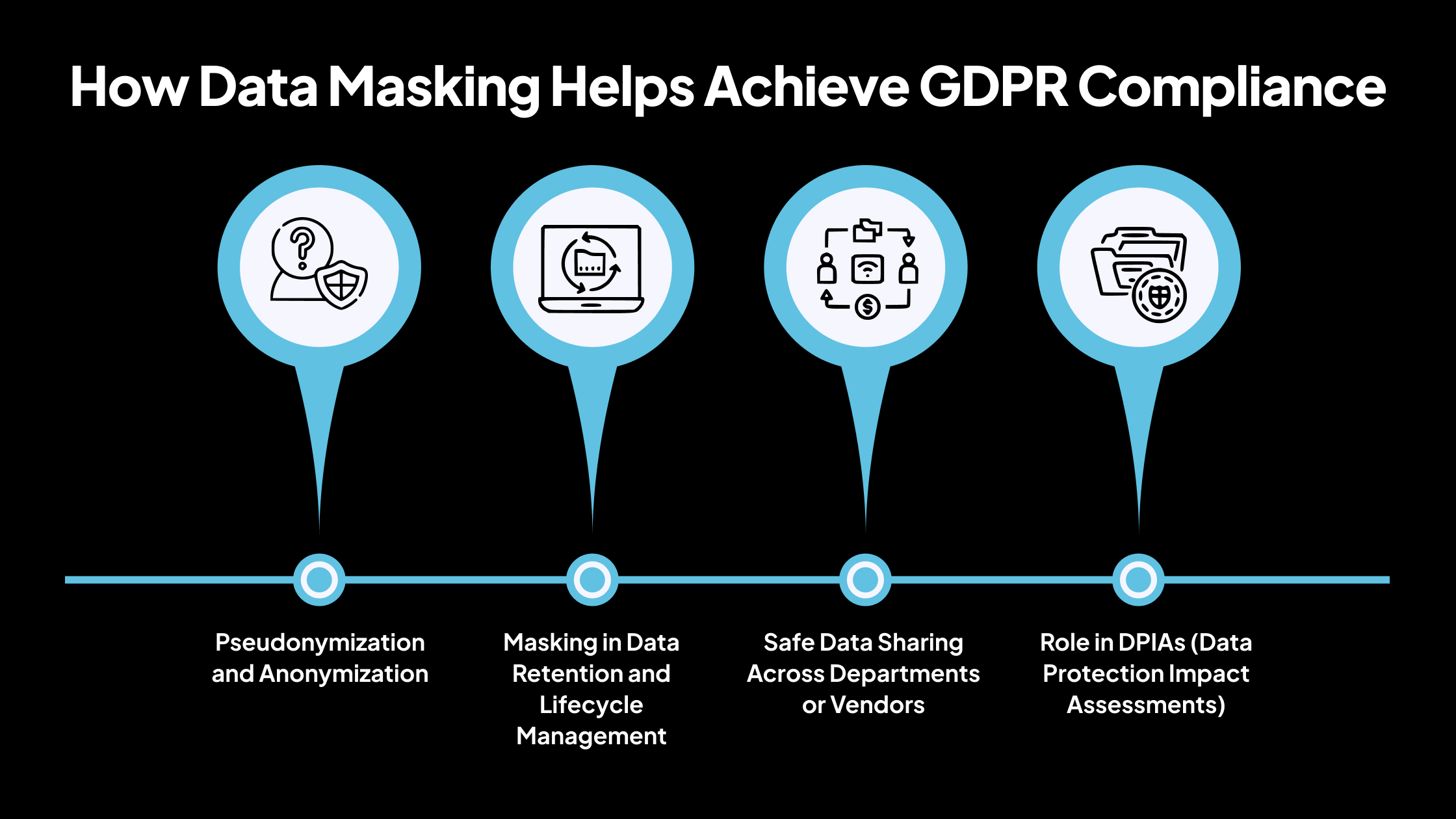
How Data Masking Helps Achieve GDPR Compliance
Data masking is a technical safeguard that supports several GDPR compliance requirements. By transforming personal data into non-identifiable formats, organizations reduce the risk of unauthorized access and ensure that only necessary data is processed. The following areas show how data masking contributes to meeting GDPR obligations.
Pseudonymization and Anonymization
Under GDPR, two key data transformation techniques are recognized: pseudonymization and anonymization. Understanding their differences is essential for determining the appropriate use of data masking.
Pseudonymization involves replacing personal identifiers (such as names or email addresses) with pseudonyms or codes. The original data can be restored using a separate key or reference table. Pseudonymized data is still considered personal data under GDPR, but is subject to reduced obligations.
Deterministic masking or tokenization techniques can pseudonymize fields, such as employee IDs, while preserving linkages for analysis. For example: “Emma Thompson” becomes “User001” in the working dataset, with the actual name stored securely in a separate, access-controlled location.
Anonymization involves removing or altering data so individuals can no longer be identified, directly or indirectly. Properly anonymized data falls outside the scope of GDPR. Masking techniques, such as random substitution or format-preserving masking, when applied without storing re-identification keys, can render datasets anonymized.
For example, a dataset of patient health records has all names, birthdates, and unique identifiers replaced with random, irreversible values, making re-identification impossible.
Masking in Data Retention and Lifecycle Management
GDPR requires that personal data be retained only as long as necessary for its intended purpose. After that, data must be deleted or rendered non-identifiable.
When deletion is not technically feasible (e.g., in backups), masking can render the data unusable and non-identifiable, aligning with the principles of storage limitation in Article 5. During archival or legacy system management, masking reduces the sensitivity of retained data without disrupting system integrity.
For example, in a CRM system, inactive user records older than 5 years are masked to remove identifiable details, while retaining the general structure for statistical analysis.
Safe Data Sharing Across Departments or Vendors
GDPR mandates that access to personal data be limited to individuals or systems with a legitimate purpose. Sharing complete datasets across internal departments or with external partners increases the risk of non-compliance.
Data masking enables organizations to share masked versions of datasets while maintaining usability for analysis, reporting, or development. This ensures the protection of personal data when outsourcing functions such as marketing, customer support, or analytics.
For example, a marketing agency receives a dataset with masked email addresses and names, but retains behavioral information for targeted campaigns. This reduces the likelihood of unauthorized access and limits the scope of data breaches if shared data is compromised.
Role in DPIAs (Data Protection Impact Assessments)
Under Article 35 of the GDPR, organizations are required to conduct Data Protection Impact Assessments (DPIAs) when processing activities are likely to pose a high risk to individuals’ rights and freedoms.
Data masking demonstrations show that the organization has implemented technical measures to mitigate data exposure risks, supporting the risk mitigation aspect of a DPIA by replacing personal data with masked equivalents in non-essential workflows.
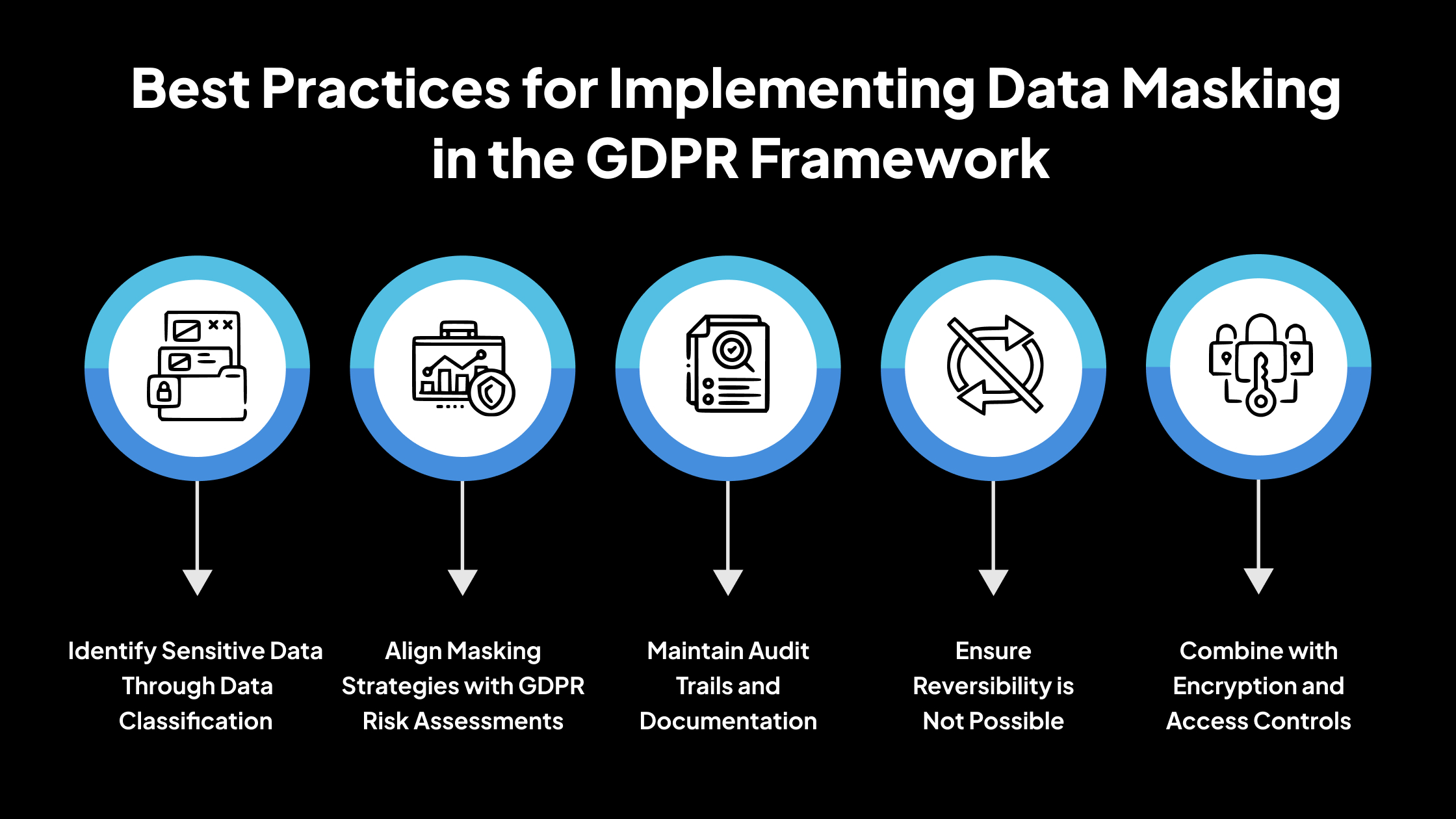
Best Practices for Implementing Data Masking in the GDPR Framework
To ensure data masking is effective and compliant with the General Data Protection Regulation (GDPR), organizations must adopt structured and technically sound practices. Below are key best practices for implementing data masking within a GDPR-aligned data protection program.
Identify Sensitive Data Through Data Classification
Before applying data masking, an organization must identify the data that requires protection. This involves identifying and categorizing personally identifiable information (PII) and other sensitive data elements such as health records, financial data, or employee information.
A formal data classification process helps segregate data into levels based on sensitivity and regulatory impact. This ensures that masking is applied precisely and only where necessary, thereby avoiding the unnecessary processing of non-sensitive data.
Align Masking Strategies with GDPR Risk Assessments
Data masking methods should be selected based on the level of risk identified through Data Protection Impact Assessments (DPIAs) or other internal risk analysis processes.
For instance, data used in software testing may require static or deterministic masking, while analytics tools may benefit more from anonymized or pseudonymized data. Aligning the masking approach with the GDPR-defined risk exposure ensures that technical controls are proportionate to the potential harm to individuals’ rights and freedoms.
Maintain Audit Trails and Documentation
GDPR requires organizations to demonstrate accountability. Therefore, every data masking activity, whether for internal testing, vendor sharing, or system development, should be logged and documented. Maintaining an audit trail includes recording when masking was applied, to which data fields, using what method, and by whom.
This documentation supports internal reviews and external audits, helping to meet the GDPR’s Article 5(2) requirement for demonstrating compliance with data protection principles.
Ensure Reversibility is Not Possible
When the goal is to anonymize data so that it falls outside the scope of GDPR, masking must be applied in a way that prevents any possibility of re-identification. This means avoiding the use of mapping keys, token references, or deterministic logic that could link masked values back to real identities.
Once anonymized, the dataset should be permanently unlinkable to the original data subject, ensuring that the data can be used safely for analytics or reporting without regulatory risk.
Combine with Encryption and Access Controls
Data masking alone may not provide sufficient protection in all scenarios. It should be part of a comprehensive security strategy that encompasses encryption, role-based access control, and robust network security measures.
While masking hides the data content, encryption protects it during storage and transmission. Access control ensures that only authorized personnel can view or modify datasets, further reducing the risk of unauthorized exposure or misuse.
Combining these measures strengthens the overall security posture and reinforces compliance with GDPR Article 32, which requires the securing of personal data.
Data Masking Challenges: What Enterprises Must Watch For
While data masking is a crucial tool for ensuring GDPR compliance and protecting data privacy, its implementation presents several technical and operational challenges. Organizations must be aware of these pitfalls to ensure that masking methods do not compromise either data utility or security.
Balancing Data Usability and Privacy
One of the core challenges in data masking is finding the right balance between data protection and usability. Over-masking can strip away valuable context, rendering the data ineffective for testing, analytics, or machine learning.
On the other hand, under-masking can leave sensitive data partially exposed, increasing compliance and security risks.
Risks of Re-Identification (Mosaic Effect)
Even after masking, there is a risk that masked or pseudonymized data can be re-identified by combining it with other datasets. This is known as the Mosaic Effect, where individual data points that appear non-sensitive can reveal personal identities when linked together.
Under the GDPR, re-identifiable data is still considered personal data, and organizations must carefully assess this risk when designing their data privacy compliance tools.
Managing Evolving Masking Rules and Misconfigurations
As data structures, applications, and compliance needs change, masking rules must be updated accordingly. Failure to update rules or incorrect implementation can result in partial masking, missing fields, or format mismatches.
For instance, a misconfigured masking rule in a CRM might leave new fields, such as “social profile link,” unmasked, leading to exposure even if traditional fields (like name and email) are adequately protected. Without regular audits and automated validation tools, misconfigurations can go unnoticed until after data is shared or exposed.
Performance Overhead in Dynamic Masking
Dynamic data masking, which masks data in real time during queries, can introduce performance issues, especially in high-traffic or large-scale databases.
There can be increased query latency due to masking logic being applied on-the-fly, compatibility issues with specific BI tools or reporting engines, and difficulty in scaling for large datasets or distributed systems.
Integration with Broader Security Measures
Data masking is only one part of an overall data protection strategy. Without integration with other security mechanisms, such as encryption, audit logging, and role-based access control, the system remains vulnerable to security risks.
Ensure data masking tools are integrated into existing security information and event management (SIEM) frameworks and encryption protocols to maintain consistent and compliant protection.
Avahi’s Data Masker: A Smart Solution for Protecting Confidential Information
As part of its commitment to secure and compliant data operations, Avahi’s AI platform provides tools that enable organizations to manage sensitive information precisely and accurately. One of its standout features is the Data Masker, designed to protect financial and personally identifiable data while supporting operational efficiency.
Overview of Avahi’s Data Masker
Avahi’s Data Masker is a versatile data protection tool designed to help organizations securely handle sensitive information across various industries, including healthcare, finance, retail, and insurance.
Why Choose Avahi’s Intelligent Data Masking Tool?
- Protects Sensitive Information Across Industries
Designed to secure financial, healthcare, retail, and insurance data, without interrupting daily operations. - Supports Regulatory Compliance
Helps meet GDPR, HIPAA, and PCI DSS requirements by anonymizing and masking personal and transactional data. - Enables Safe Data Sharing
Ensures only authorized users, internal or external, can access real data through role-based access controls. - Preserves Operational Efficiency
Allows development, analytics, and fraud detection teams to work with realistic, non-sensitive data formats. - Reduces Risk of Data Breaches
Minimizes exposure of real data in test environments, vendor interactions, and cross-department workflows. - Integrates Seamlessly with Enterprise Workflows
Applies masking without disrupting backend processes, ensuring business continuity and productivity.
Simplify Data Protection with Avahi’s AI-Powered Data Masking Solution
At Avahi, we recognize the crucial importance of safeguarding sensitive information while maintaining seamless operational workflows.
With Avahi’s Data Masker, your organization can easily protect confidential data, from healthcare to finance, while maintaining regulatory compliance with standards like HIPAA, PCI DSS, and GDPR.
Our data masking solution combines advanced AI-driven techniques with role-based access control to keep your data safe and usable for development, analytics, and fraud detection.
Whether you need to anonymize patient records, financial transactions, or personal identifiers, Avahi’s Data Masker offers an intuitive and secure approach to data protection.
Ready to secure your data while ensuring compliance? Get Started with Avahi’s Data Masker!
Frequently Asked Questions
1. What is GDPR-compliant data masking?
GDPR-compliant data masking is the process of transforming personal data into non-identifiable formats, such as pseudonymization or anonymization, so it cannot be linked back to an individual without additional information. It helps meet GDPR requirements under Articles 5, 25, and 32 by securing sensitive data in development, testing, or analytics environments.
2. How does data masking help with GDPR breach notification requirements?
If data involved in a breach is properly masked or pseudonymized, organizations may not be required to notify authorities or affected individuals under Articles 33 and 34 of the GDPR. Masking significantly reduces the risk of harm by rendering the breached data unintelligible and unlinkable to any specific person.
3. What types of personal data should be masked under GDPR?
Organizations should mask personally identifiable information (PII) such as names, email addresses, phone numbers, Social Security Numbers, account details, and health records. These data types fall under GDPR’s definition of personal data and must be protected from unauthorized access.
4. What’s the difference between data masking, pseudonymization, and anonymization under GDPR?
Data masking is a technique used to hide sensitive data. Pseudonymization replaces identifiers with codes but allows re-identification through a key. Anonymization permanently removes identifiers, making data irreversible and no longer subject to GDPR. Masking can support both, depending on the implementation.
5. Is data masking alone enough for GDPR compliance?
No, data masking should be part of a broader GDPR compliance strategy. It must be combined with encryption, access control, audit logging, and regular risk assessments to meet GDPR’s technical and organizational measures required under Article 32.